A Web Application Firewall (WAF) is a tool for protecting applications from web attacks at the application layer. It analyses HTTP/HTTPS traffic and XML/SOAP semantics, ensuring robust protection for your organization’s apps. WAFs are available with a range of additional features, for example load balancing or intrusion prevention.
This article examines the role of WAF in detecting and blocking malicious traffic to web applications.
What is WAF?
A Web Application Firewall (WAF) is a type of firewall specifically designed to monitor and protect web applications from potential threats. It monitors HTTP and HTTPS traffic for any anomalies, suspicious behavior or attacks, providing an additional layer of security for web-based systems. The primary distinction between a firewall and other forms of protection is that it offers comprehensive analysis of protocol traffic at the application layer.
Typically, WAF is deployed on the network, hosted on a server, or in the cloud, and can be integrated through a reverse proxy on a site or application. WAF is a form of Layer 7 protocol protection. The technology can rapidly identify and protect websites from the most malicious attacks, where IDS and IPS are ineffective.
How does WAF work?
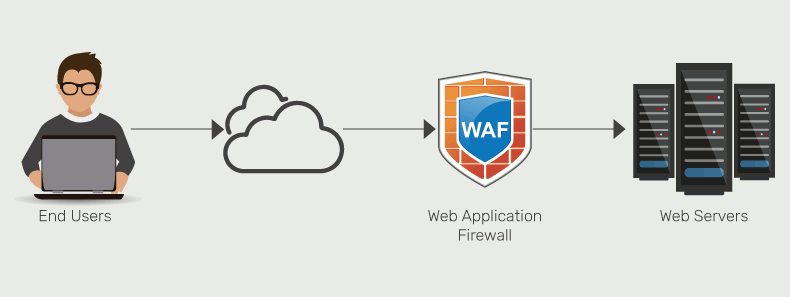
A WAF is deployed in front of a web application, acting as a cybersecurity shield between it and the Internet. In contrast to a standard proxy a WAF functions as a ‘reverse proxy’. This process ensures that the server is safeguarded by inspecting all incoming traffic before allowing clients to access the application.
There are three methods for analysis and filtering HTTP content.
Whitelisting
By default, the tool rejects all requests and only allows trusted. This method is simpler than blacklisting, but there is a risk of blocking legitimate traffic.
Blacklisting
This method involves disclosing default data and utilizing preset methods to block malicious internet traffic. Therefore, it entails the implementation of specific criteria that may signify potential risks. Such approach is better suited to public websites, which typically receive a high volume of traffic from a range of IP addresses.
Hybrid
This approach combines the advantages of the whitelist and blacklist methods.
Key Security Threats Addressed by WAF
Injections of PHP code. Such vulnerabilities permit attackers to inject and execute third-party code on a server, which can ultimately result in system compromise.
Cross-site scripting (XSS) is a type of cyber-attack that involves injecting malicious code into web pages. This code can perform a range of actions, including stealing user data or carrying out unwanted operations on their behalf.
SQL injection is a common attack targeting websites and applications that work with databases. The essence of the attack is that an attacker inserts malicious SQL code into a query to gain access to a database and manipulate it.
Brute-force attacks aim to brute force passwords, session IDs, and attempt to perform DoS attacks.
Automated actions involve picking up logins and passwords, promo codes, and other data. For example, in online shops, this can result in items being automatically added to the cart to deplete stock.
Bots scan web applications for vulnerabilities, extract data, and perform other malicious activities. They create a significant amount of malicious traffic on the internet.
Benefits of WAF
A web application firewall plays a vital role in building a robust security system. Without this tool, a business is vulnerable to cyber attacks. Below are some of the benefits of a web application firewall:
1. Protection against unknown vulnerabilities.
Attackers are able to retrofit attacks in a way that a simple antivirus would not recognize, making it crucial to have a WAF with machine learning capabilities to detect unfamiliar types of attacks.
2. Preventing SQL Injections
SQL Injection occurs when an attacker modifies queries executed by an application, thereby gaining access to sensitive information. WAF employs a set of rules that require SQL Injection to meet specific conditions. If it does not, the user is will not get access to the web application.
3. Risk minimization.
In contrast with intrusion detection systems, WAF not only performs a more in-depth analysis of web protocols, but also eliminates threats.
4. Preventing DDoS attacks
During a DDoS attack, multiple malicious devices are used to overload the web application, creating an abnormally high volume of traffic. This results in a denial of service for normal traffic.
WAF is able to detect and prevent this type of activity based on indicators such as high traffic volumes from a specific IP address, unusual traffic patterns, or high traffic on a particular page.




