DDoS (Distributed Denial of Service) attacks are a serious threat to web resources and companies. They can cause a website or online service to become temporarily unavailable. In this article, we will look at the different types of DDoS attacks.
Types of DDoS
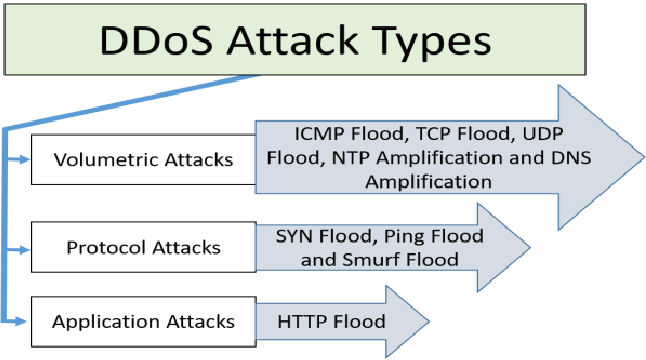
There are three levels of DDoS attacks, depending on the target.
-
Application Layer. These attacks target specific applications or services. In an application-level attack, the intruders make many fake requests to a specific part of the website or service, causing it to hang or even crash. Real users will not be able to use it.
-
Protocol Layer. As the name suggests, the vulnerability is in the protocols used by the server. Attacks of this type are aimed at absorbing the resources of the server or intermediate servers (devices). The essence of the attackers' actions is simple - while the packets sent by the hacker are being processed, packets from users are waiting for their turn. If the number of packets sent by the attackers significantly exceeds the number of packets sent by normal users, the time that users wait for a response from the server becomes prohibitively long.
-
Transport Layer. A DDoS attack targets the network layer of a server or web resource. The aim is to cause a tablespace overload on a firewall, central network or load-balancing system.
The most common method of DDoS at the transport layer is network flooding - the creation of a huge flood of requests at different layers that the receiving node cannot physically handle.
Normally, the network service applies the first-in, first-out (FIFO) rule, where the computer does not serve the second request until it has served the first. However, when an attack occurs, the number of requests increases to such an extent that the device does not have the resources to complete the first request. As a result, flooding maximises bandwidth saturation and clogs all communication channels.
DDoS attacks examples
Ping of death. This attack involves sending an echo request that exceeds the allowed size of 65535 bytes. The device will not know how to deal with such a request and will stop responding to it. Currently, ping of death is no longer used - the size check during packet assembly has solved the problem. Packets over the allowed size are discarded. This attack belongs to the class of DoS attacks because the sender is a single computer and not a network of different devices as in a DDoS attack.
HTTP flood. Each botnet node generates a large number of HTTP requests to the server, greatly increasing the load. These can be either GET or POST requests. In GET requests, the client requests the heaviest parts of the site. In POST requests, it sends large amounts of data to the server in the body of the request.
ICMP flood. The attacker's botnet overloads the victim's host machine with service requests, forcing it to provide echo responses. A common example of this type of attack is a ping flood or smurf attack, where communication channels are flooded with ping requests to check the availability of a network host. Because of the threat of ICMP flooding, system administrators often use a firewall to completely block the ability to make ICMP requests.
UDP flood. Random ports on the victim's host machine are flooded with UDP packets, the responses to which overload network resources. A type of UDP flooding directed at a DNS server is known as DNS flooding.
SYN flood. The client sends a large number of SYN packets with a spoofed IP address to the server. The server responds to each request and waits for the client to connect. The client ignores the invitation and creates new requests, causing the connection queue to overflow. As a result, the server's performance drops to the point where it stops working altogether.
DNS amplification. Attacking devices send small queries to public DNS servers. The queries are crafted so that the response contains as much data as possible. In addition, the query spoofs the IP address of the real sender to the victim's address, to which the DNS server will send the responses. As a result, the victim receives many large data packets from the DNS server, causing channel overflow.
Cloud4U employs advanced DDoS mitigation techniques to help prevent attacks before they reach your target applications, networks and infrastructure. With our DDoS protection solution, you can keep your websites and online services running smoothly and stay ahead of attackers.




